What is Ping? How to Ping?
In the digital world, an important tool for testing network connections and diagnosing issues is the “ping” command. So, what is ping and how is it used? In this article, we will comprehensively explore what the ping command is, how it works, its advantages, and the steps to perform a ping.
What is Ping?
Ping is a network tool used to test the health and performance of a network connection. The term “Ping” is an abbreviation for “Packet Internet Groper” and provides information about the status of the connection with the target device through the sending and receiving of data packets over the network. The ping command is commonly used to diagnose network connection issues in computer networks and over the internet.
Ping sends data packets to a network device (such as a server, router, or another computer) and expects the device to send these packets back. This process is used to measure the speed, reliability, and latency of the network connection. It can also help determine if the target device is offline or if there is an issue with the network.
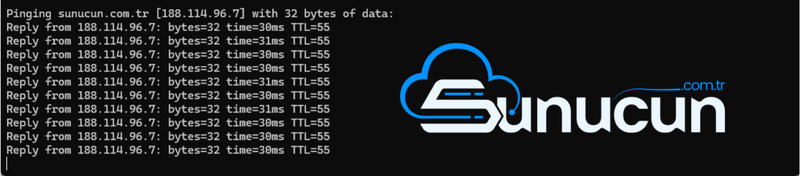
How Does Ping Work?
The operation of the ping command is quite simple and generally involves the following steps:
- Executing the Ping Command: The ping command sends a data packet to a network device. This command is usually executed from the command line or terminal. For example, an IP address or domain name is specified.
- Sending Data Packets: The ping command sends ICMP (Internet Control Message Protocol) Echo Request packets to the target device. These packets are designed to prompt the target device to respond over the network.
- Receiving Responses: The target device sends Echo Reply packets in response to the incoming Echo Request packets. These responses appear as latency and other information in the ping command output.
- Displaying Results: The ping command displays the number of packets sent, the number of responses received, latency times, and any packet loss. This information provides insights into the performance of the network connection.
Advantages of the Ping Command
The use of the ping command offers several advantages:
- Diagnosing Network Connection Issues: Ping is an effective tool for diagnosing network connection problems. If a target device cannot be reached, it helps determine if there is a problem with the network.
- Measuring Latency: The ping command is used to measure network latency. This helps assess internet speed and network performance.
- Detecting Packet Loss: Ping can detect packet loss, which can indicate problems with network performance.
- Checking the Target Device’s Status: Ping can check whether a device is offline or not. This provides information about the status of the target device’s network connection.
How to Perform a Ping Using the Ping Command
Performing a ping with the ping command is quite simple and generally involves the following steps:
- Accessing the Command Line: To execute the ping command, you need to access your computer’s command line or terminal. On Windows operating systems, “Command Prompt” or “PowerShell” is used, while “Terminal” is used on macOS and Linux systems.
- Entering the Ping Command: Enter the ping command along with the target IP address or domain name into the command line or terminal. For example:
ping sunucun.com.tror
ping 8.8.8.8 - Examining the Results: When the command is executed, ping results are displayed on the screen. These results include the number of packets sent, the number of responses received, the latency of each response, and any packet loss.
Additional Parameters for the Ping Command
Some additional parameters that can be used with the ping command to make your tests more detailed:
- -t: On Windows systems, adding the “-t” parameter to the ping command allows continuous pinging, which can be stopped by pressing “Ctrl + C”. For example:
ping -t sunucun.com.tr - -c: On macOS and Linux systems, the “-c” parameter specifies the number of ping packets to send. For example:
ping -c 10 sunucun.com.tr - -l: On Windows systems, the “-l” parameter sets the size of the packets sent. For example:
ping -l 1024 sunucun.com.tr - -i: On macOS and Linux systems, the “-i” parameter sets the interval between ping packets. For example:
ping -i 2 sunucun.com.tr
Common Issues and Solutions with Ping
Some common issues you might encounter when using the ping command and their solutions:
- Packet Not Received: If no response is received when pinging the target device, there may be a problem with the network connection. In this case, check the network cables and device connections.
- High Latency: If the ping response time is high, there may be a delay issue in the network. In this case, check your network hardware or internet service provider to improve network performance.
- Packet Loss: If packet loss occurs, it may indicate a problem with network performance. This is a sign to check the network hardware or connection.
Security Implications of the Ping Command
There are also some security aspects of the ping command:
- Testing and Analysis: The ping command can be used to identify potential security vulnerabilities on the network. For example, checking if a device on the network responds can be an initial step for network security.
- Attack Detection: The ping command can be used to detect high-volume ping attacks (Ping Floods) targeting a device. Such attacks can make it difficult or impossible for the target device to respond.
Conclusion
Ping is a powerful tool used to assess network connection performance and diagnose network issues. By using the ping command, you can measure the health of your network connection, latency times, and packet loss, thus improving your network’s performance. Properly using the ping command allows you to quickly resolve network issues and make your network connections more efficient. Ping, as a simple yet effective tool, is a cornerstone of network management.




